



Get your team started in minutes
Sign up with your work email for seamless collaboration.

In modern enterprises, Identity and Access Management (IAM) plays an absolutely essential role as the foundation of cloud security frameworks It directly shapes how everyday users, reliable services, and key applications consistently interact with cloud resources, guaranteeing only the right and verified entities receive smooth access. Without implementing strong IAM controls, even the most advanced forms of cloud computing security architecture stay vulnerable to malicious breaches, potential insider threats, and harsh compliance violations.
IAM in cloud architecture is a framework of policies and technologies that governs identity verification and access permissions.Identity and Access Management is not confined only to basic user accounts; it naturally extends to APIs, background services, and critical machine identities we depend on daily. When access control is centralized, IAM helps maintain consistent, human-trusted enforcement of security policies across all major cloud providers.
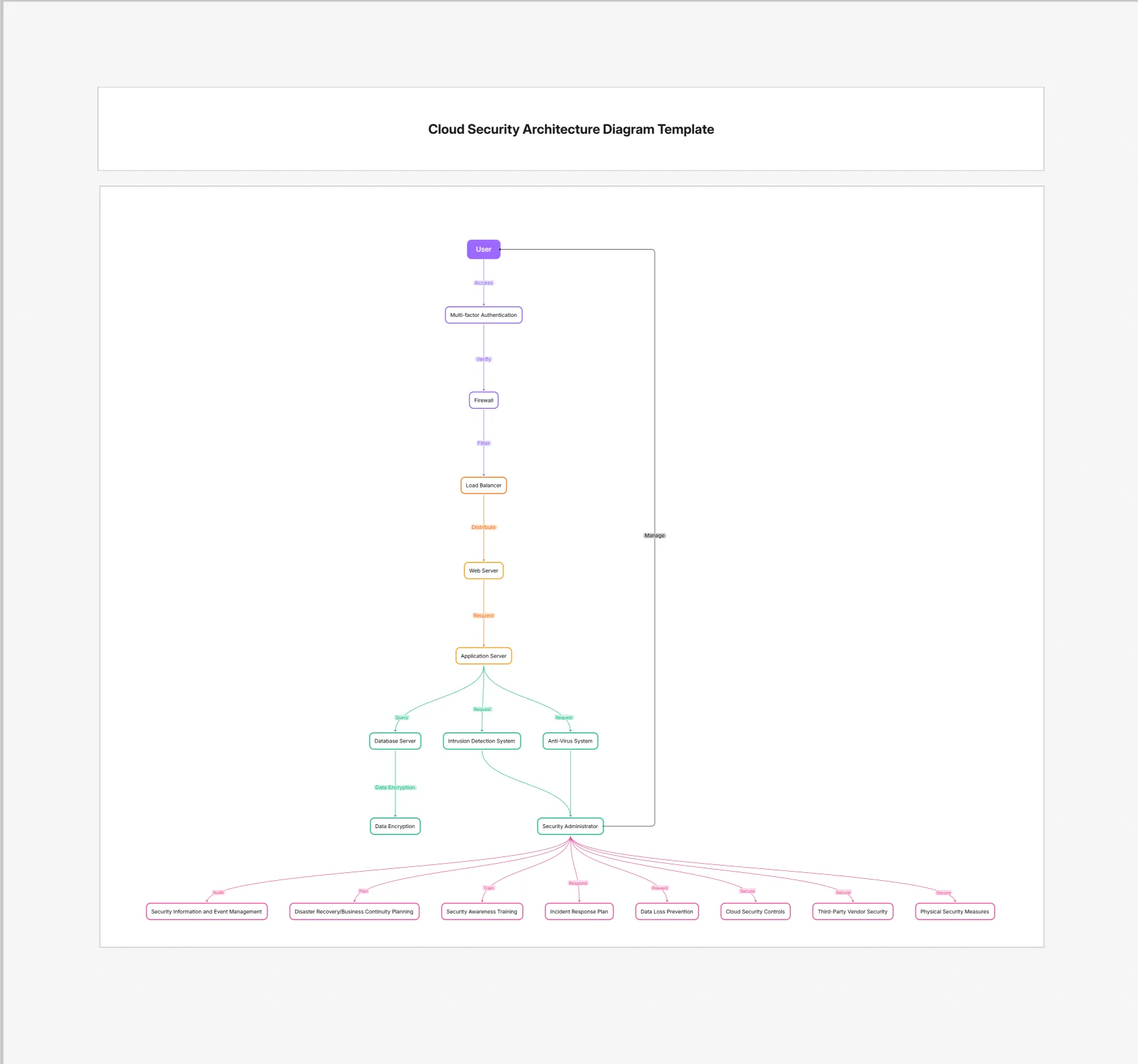
Template: IAM Architecture in Cloud Computing Template
An IAM design is most secure when it follows principles that manage risk and ensure responsibility.
Even though the core fundamentals of IAM remain consistent, I’ve noticed that each cloud provider has its own set of specialized services and workflows for putting those fundamentals into action.
Related templates:
IAM is definitely more than just another feature it serves as the true backbone of cloud computing security architecture today. It guarantees proper compliance, stronger data protection, and seamless operational consistency across multiple workloads.
you can also use this Cloud Security Architecture Template.
Enterprises like ours can strengthen IAM smartly by adopting proactive strategies carefully tailored for complex business environments.
Cloudairy provides ready-to-use templates that simplify IAM planning and design.
IAM is the foundation of cloud security architecture. It protects workloads, enforces compliance, and integrates with broader cloud computing security architectures. By using Cloudairy’s Cloud Architecture Diagram Tool and related IAM templates, enterprises can design robust security models that scale across AWS, Azure, and GCP.
Start designing secure IAM architectures with Cloudairy.
Start using Cloudairy to design diagrams, documents, and workflows instantly. Harness AI to brainstorm, plan, and build—all in one platform.
.webp)
.webp)
.webp)