



Get your team started in minutes
Sign up with your work email for seamless collaboration.
Financial institutions process money, credit, and identity at scale prime targets for well-funded attackers and fraud rings. A resilient security architecture in finance must reduce blast radius, contain credential abuse, and prove compliance without slowing transactions. Designs lean on Zero Trust patterns, granular segmentation, and continuous evidence capture tied to payment and customer journeys. When aligned with business risk, this approach lowers fraud losses, streamlines audits, and protects customer trust across channels.
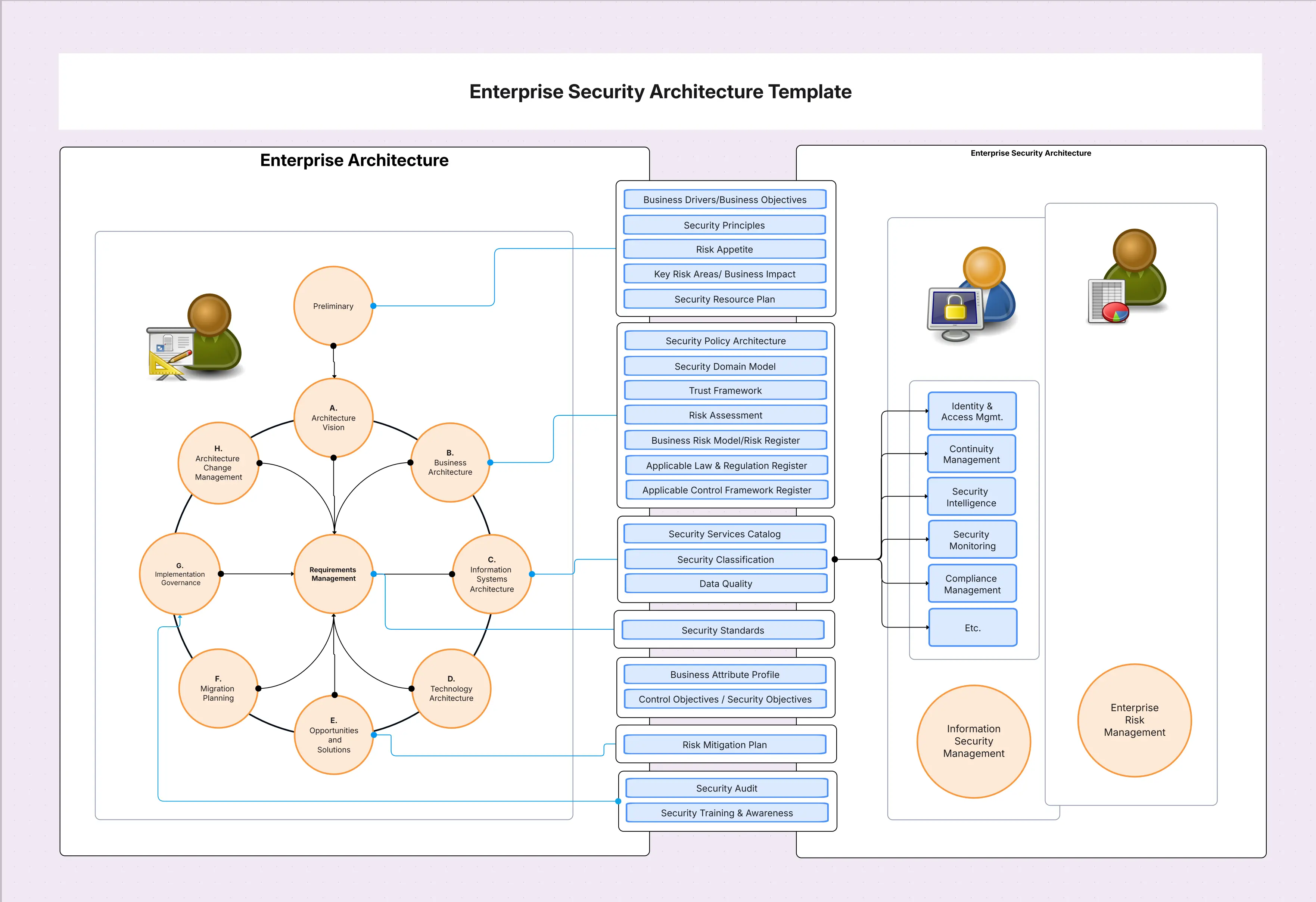
Model the target state with the Enterprise Security Architecture Template inside the Security Architecture Diagram Tool. Deep-link to Zero Trust, IAM, Network Security, Security Monitoring, and Hybrid Cloud Security.
Banks and fintechs face credential stuffing, account takeover, insider misuse, mule networks, and API fraud often blended with social engineering and malware. Regulations add pressure: PCI DSS for card data, FFIEC guidance for resilience, SWIFT CSP for interbank transfers, and local privacy laws. A financial security architecture must unify controls across branches, call centers, mobile apps, and cloud services. The result is an evidence-rich posture that satisfies auditors while blocking revenue-impacting attacks.
Finance rewards designs that are strict under the hood but smooth for customers. Lead with protection surfaces: payments, onboarding, and high-value data. Enforce identity-first access and just-in-time privilege so standing risk stays small. Keep data confidential and provable with encryption, signing, and strong key management. Finally, build an observability loop that marries fraud analytics with security telemetry for fast, automated action. Principles should translate into measurable loss reduction not just documents.
Prioritize assets that move money or unlock credit. Map request paths end-to-end, then narrow routes with gateways, strong auth, and microsegmentation. Use risk signals velocity, device health, geolocation to trigger step-up checks at sensitive steps. Instrument every decision so disputes and chargebacks can be resolved with evidence rather than guesswork, keeping customer friction proportional to risk.
Make identity the control plane. Centralize workforce and customer identities, enforce phishing-resistant MFA for admins, and prefer passwordless for scale. Replace standing admin with short-lived elevation tied to tickets and approvals. Bind tokens to device posture and keep lifetimes brief. With IAM Architecture and Zero Trust, access follows context, not networks.
Encrypt data in transit and at rest; tokenize PANs and sensitive attributes. Use HSMs or cloud KMS for keys, rotate frequently, and segment access to minimize blast radius. Sign critical messages (payments, consents) to ensure integrity and non-repudiation. Tie data access to business purpose and retention policies so privacy obligations are met without blocking analytics.
Unify SIEM/XDR telemetry with fraud signals—behavioral biometrics, device fingerprints, and anomaly scores. Build SOAR playbooks to freeze risky sessions, expire tokens, or step-up auth automatically. Feed outcomes to models and policies so detections get sharper. With the Security Monitoring Architecture, investigations move from days to minutes and losses trend down.
Use a layered, evidence-driven design that starts at digital channels, passes through identity and policy engines, and reaches payment cores through segmented paths. The numbering below matches components you can drag into the Enterprise Security Architecture Template and cross-link to Network, IAM, and Zero Trust so identity decisions and routes remain consistent.
Deliver value in quarters, not years. Pick one protection surface, ship end-to-end controls, and prove reduced loss or faster response. Then scale the pattern. The steps below align to the Security Architecture Diagram Tool so architecture, operations, and compliance share the same living blueprint.
Audits move faster when evidence maps directly to controls and owners. Use automation to collect logs, configs, and tests so proofs are click-to-export. The mappings below help you show clear alignment between architecture choices and regulatory expectations.
Most failures are operational, not conceptual. The traps below pair a symptom with a fix you can execute this quarter—without stalling the roadmap.
Pick metrics leadership understands and operations can influence weekly. Show directional improvement and tie it to shipped controls.
Fewer repeat findings and faster remediation demonstrate durable governance. Tie each closeout to an owner and architectural control.
Finance runs on trust and trust runs on evidence. A modern security architecture in finance narrows routes to money, ties access to identity and context, and proves every decision with telemetry. Start with one high-value journey, ship end-to-end controls, and show reduced loss or faster response. Build your blueprint with the Enterprise Security Architecture Template in the Security Architecture Diagram Tool, then scale across channels, partners, and clouds.
1. How is financial security architecture different from generic enterprise security?
2. Can Zero Trust work with legacy cores and mainframes?
3. Where should a mid-size fintech start?
4. How do we balance fraud controls with customer friction?
5. Which templates should we use to model this?
Start using Cloudairy to design diagrams, documents, and workflows instantly. Harness AI to brainstorm, plan, and build—all in one platform.
.webp)
.webp)
.webp)